File Integrity Monitoring
Detect, monitor, and remediate changes with system integrity assurance
IT Security And Compliance
- Windows Registry
- Drivers
- Installed software
- Security Policies
- Services
- Network Share Files
- Network Share configuration
- Local Users / Groups
- Active Directory / LDAP
- Microsoft Exchange
- Network Devices - Firewalls, Switches, Routers
- Hypervisors - ESXi, HyperV, XenServer
- Databases -MSSQL, Oracle, MSQL, Maria DB, IBM DB2
Why File Integrity Monitoring (FIM)
Organizations implement a File Integrity Monitoring solution for various reasons, like securing active directory and system files, data security, including zero-day attacks, and meeting the regulatory compliance standards or objectives with various regulations such as PCI-DSS, HIPAA, SOX, NERC, FFIEC, FISMA, GDPR, CMMC, CDM, SWIFT and more.
File integrity monitoring (FIM) is a crucial security practice that involves monitoring and analyzing changes to critical files on a system to detect and prevent unauthorized modifications or access. By regularly scanning and comparing the current state of files against their known, trusted baseline, FIM tools can quickly identify any unauthorized changes, such as tampering or malware infection, and alert security teams to take necessary actions.
FIM can be implemented using a variety of techniques, such as checksums, digital signatures, or behavior-based analysis, and can be performed on both on-premises and cloud-based systems. Additionally, FIM can provide compliance benefits by helping organizations demonstrate adherence to regulatory requirements, such as PCI DSS and HIPAA.
Overall, effective FIM is a critical component of a comprehensive cybersecurity strategy, and organizations of all sizes should consider implementing FIM solutions to protect their valuable data and systems from unauthorized access and modification.

Working From A Trusted Baseline

File Integrity in Real-time
CimTrak continuously monitors changes in real-time and responds instantly to unexpected/unwanted changes. Proactively prevent cyberattacks at the source without restricting operations to reactive threat feeds.

Complete Change Detail
CimTrak pinpoints exactly what has changed and provides complete change audit information. Forensic details provided with changes include; Who changed the information, What exactly changed, When it was changed, the process used to change it, and How.
Change Management/ Change Control
CimTrak can pinpoint exactly what changed and provide complete change audit information. Knowing a change happened is of little use without understanding the corresponding metadata associated with the change.
Advanced file integrity monitoring (FIM) solutions like CimTrak give a deeper dive into unauthorized changes by not only letting you know exactly what changed but also other forensic details such as:
WHO changed the information, WHAT exactly changed, WHEN it was changed, and the process used to change it, and HOW.
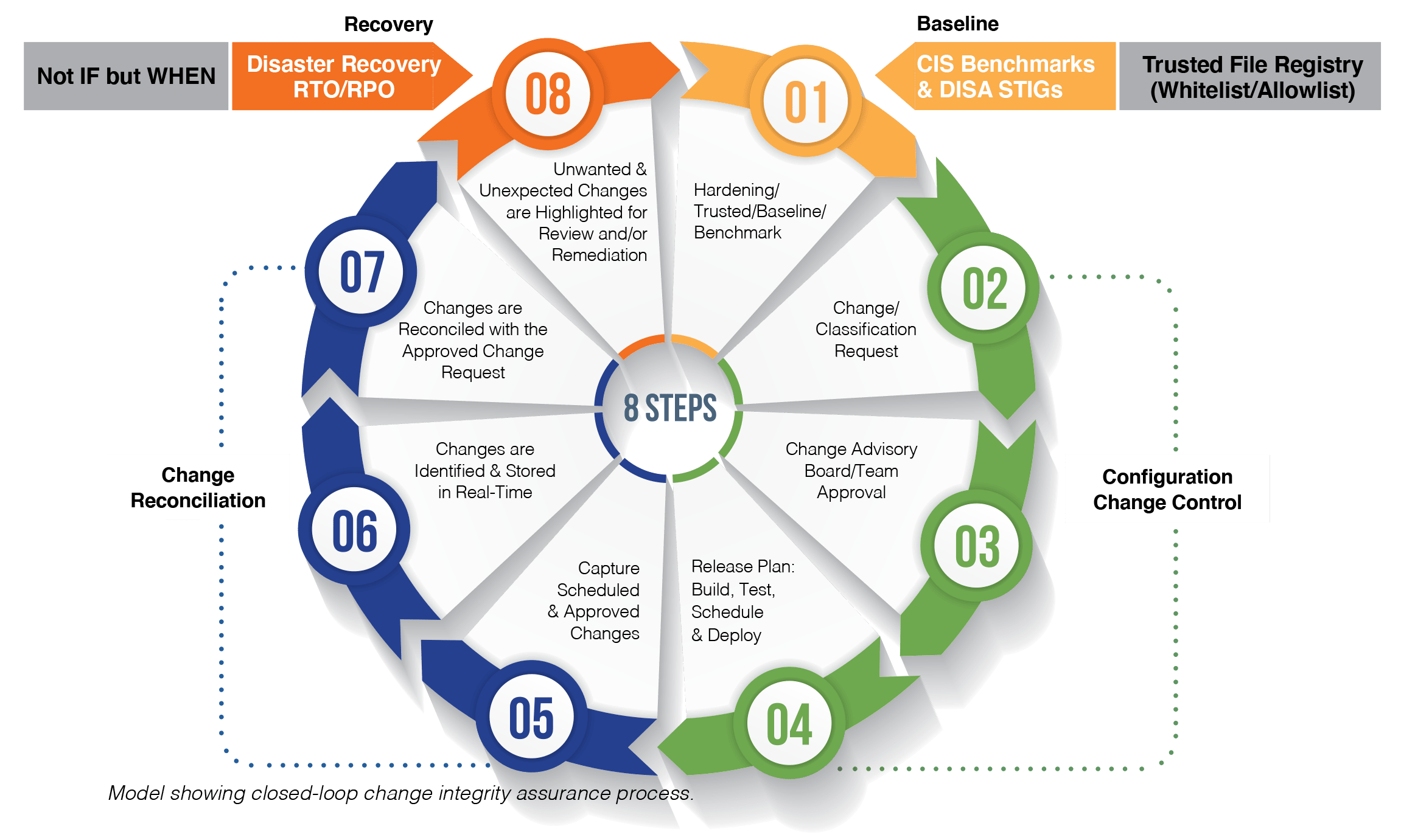
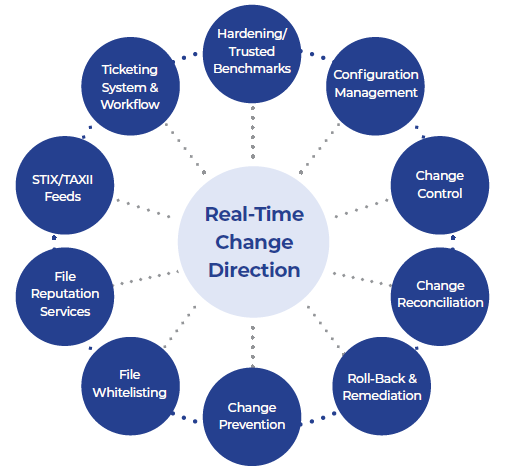
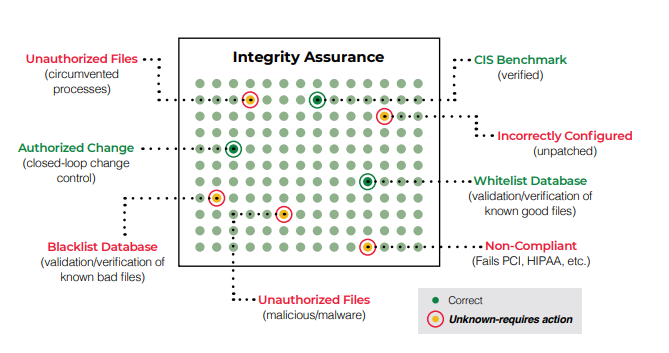
System Integrity Assurance
System Integrity Assurance (SIA) is the next evolution of FIM. It establishes a known, trusted, and authoritative baseline of what is allowed and then prevents, limits, or rolls back everything else. With true detection and response, whenever an unknown, unwanted, or unexpected change occurs, it’s managed by exception so that authorized changes are added to the baseline while malicious activity or unacceptable changes are highlighted for investigation and/or remediation.
- True real-time change detection and response
- Integrated ticketing capabilities allow the classification of changes, maximizing security by focusing attention on the most critical changes
- Trusted File Registry™ service allows automatic reconciliation of known vendor updates and patches, resulting in significant time savings
SIEM Integration and More
CimTrak helps SIEMs do their job better by receiving system, application, and file change data directly from the file integrity monitoring tool itself.
This allows the SIEM to combine critical change information with other data streams, allowing for enhanced event analysis and correlation. Benefits include learning about security events more

FIM And PCI – What’s the Connection?
PCI DSS and file integrity monitoring fit together like a hand in a glove. Specifically, sections 10.5.5 and 11.5 require
PCI DSS 11.5
Deploy file integrity monitoring software to alert personnel to unauthorized changes of critical system files, configurations files, or content files; and configure the software to perform critical file comparisons at least weekly.
PCI DSS 10.5.5
"Use file integrity monitoring or change-detection software on logs to ensure that existing log data cannot be altered without generating alerts …"
Security professionals know unexpected changes can mean that something bad is happening to your system. With new forms of malware continuously being unleashed, much of it being zero-day, it is critical that you have technology in place to detect such threats.
As these threats are unsignatured, many will find their way through perimeter defenses and attempt to take up residence in your infrastructure. Each day seems to bring news of the latest breach of payment card data. Proactively being alerted to changes can mean the difference between eliminating a threat quickly, or losing your customer’s personal information.





